Working more and more digitally and conducting digital transactions, the digital transition, has been accelerated by the Corona crisis. It seems that we are not going back to the way things were. This calls for a new and broader view on IT security.
The impact of the Corona crisis
While we wait for redemption by a Corona vaccine, remote working is the norm for anyone who can do his or her job digitally. The question is whether after this period we will pick up the thread of the past and leave the newly discovered digital facilities for what they are. Will we happily travel to and from the office in the morning and evening rush hour and want to meet our colleagues, clients, pupils, students and patients face to face again for everything that requires contact?
That seems unlikely to me. Apart from all the health, social and economic misery that the Corona Crisis entails, one positive effect is that we will realise that our technology has reached a level where we can save time by working differently. This realisation will lead us to continue working remotely and to make increasing use of the new possibilities.
Security must be broader
What does this mean for the security of our IT? One thing is clear: protecting and inspecting organisational networks is no longer enough. It hasn’t been for some time, yet many organisations have stuck to IT security measures such as firewalls, monitoring and inspecting network traffic. Now is the time to broaden those measures. After all, we work with a growing variety of cloud services and, in addition to an office workplace, with an increasing number of different devices. Their security requires broader measures.
Zero-trust
It is good to realise that security in IT is about information and, more specifically, that it is available when you need it, cannot be accessed when and where it is not wanted and cannot be changed when it is not wanted. We exchange information through means such as video conferencing, e-mail, apps, web transactions and often store information in several places simultaneously. This information ends up in databases, on file servers, in log files of the service provider and with the users on their smartphones, computers, back-up disks, and so on. The information we use is therefore spread across many locations within and outside the organisation’s network.
For several years IT analysts and IT suppliers have been trying to convince their customers that a more holistic approach to IT security is needed, one that takes into account modern ways in which ‘ordinary’ users, developers and IT administrators work with IT.
A good overview of where to look at security is the zero-trust model from market analyst Forrester. This model also states that security may never be based on assumptions and that the question must always be asked whether a chosen or existing security measure is sufficient. Apparently, this makes security more complex and more expensive, but the opposite can also be the case. All too often, measures that are too heavy are taken on the basis of assumptions. A proven method to test such assumptions is a risk analysis, in which the probability and consequences of such an assumption are weighed against the costs of the countermeasure.
The zero-trust model indicates that the chain consists of, successively:
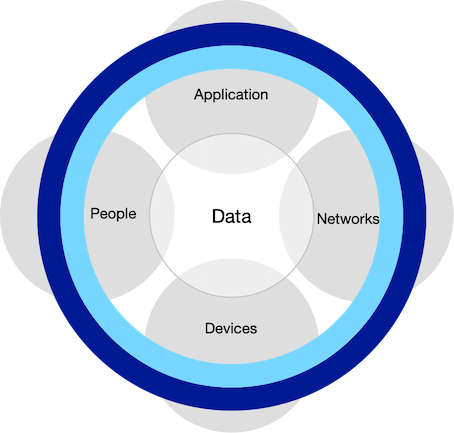
Measures can be taken in each section to ensure safety. The measures can be of an organisational or technical nature. Organisational measures are, for example, agreements laid down in contracts, the supervision thereof and the design of work processes. The characteristic of modern technical measures is that they make use of tools that analyse how IT resources are used and that work processes are automated as much as possible to prevent human errors.
The analyst Gartner adds something important to the zero-trust model: look closely at where trust does exist. Where you have trust, for example in your own employees, in a cloud provider or in the security of your smartphone, you need to secure less. But according to zero-trust, trust should never be based on assumptions, always on concrete facts.
Determining the degree of trust is also part of the risk analysis.
Risk Analysis
For decades, it has been common practice for organisations to carry out risk analyses, in order to identify threats and weigh up whether measures should be taken in response to them. Measures are assessed for cost and feasibility and must be compared with the damage a threat can cause and the probability of that damage occurring. It is not an easy job and, as threats change, it has to be repeated again and again, but organisations are already used to doing it. There are two questions of importance in view of the present time:
- Are organisations doing a risk analysis at the right levels? Do they look at the whole chain of the zero-trust model?
- Do organisations take sufficient account of trust in people and suppliers?
Working on risk analyses for the entire chain can make security a lot more expensive, but making trust in people and suppliers explicit can also make security cheaper.
Threats
A good risk analysis stands or falls with the proper mapping of all threats. For threats related to vulnerabilities in devices and applications, it is important to follow which ‘patches’ are released and get them installed on time. These are often serious threats because hackers can use them to gain control over a device or applications. In general, these vulnerabilities only become public knowledge once a patch has been issued. This is partly because suppliers offer large sums of money if (ethical) hackers report them. What is worrying is that hacking is also a business these days and that there are malicious organisations that offer money for knowledge of a vulnerability that has not yet been published. But so far the effects have not been very great. Very occasionally, a supplier is too late with a patch for a zero-day vulnerability, as they are called when they have just been discovered. Then emergency measures have to be taken.
But in addition to these threats, there are many others that have to do with human behaviour:
- Manipulation via social media or phishing can lead to great damage.
- Careless handling of passwords can cause a lot of misery. . In fact, a hacked account is often the start of worse, such as ransomware, stealing information, etc. It is a serious threat to everyone, because we are all human and do not use passwords as we should. In addition, ‘forgotten password’ procedures are often not watertight.
- Careless distribution of rights is a problem, because users can cause a lot of damage by consciously or unconsciously leaking information or changing information. More than half of all security incidents at organisations fall into this category! And is therefore not caused by an external attack.
- Careless handling of ‘unstructured data’, the loose documents we use every day, is a serious problem. We usually set permissions on folders containing documents and not on the documents themselves. But who says users always keep sensitive documents in the right place?
- Letting a family member use a device. What can happen then?
These are just some of the concrete threats that exist today. The threats are also constantly changing as IT innovates and new opportunities arise to consciously or unconsciously leak, alter or reduce the availability of information. It is important to keep a close eye on this.
Users, devices and information
Organisations need to take a broader view of their risk analyses and include the behaviour of people, the use of their devices and the information itself.
Fortunately, the IT market has not been idle and there is a good range of solutions that can reduce these risks. The solutions can be found in the field of Identity & Access Management (user accounts and rights and access security), Endpoint security (devices), Data Management (getting a grip on the information) and Data Governance (insight into what information there is and where it is). It would be going too far to go into detail here as to what these solutions can offer, but because the user is central here, all solutions have an impact on the work processes to a greater or lesser extent and therefore require a good organisational implementation in addition to a technical realisation.
What should you invest in?
Market analyst KuppingerCole gives advice in this vlog.
Capitar Security helps
At Capitar Security we like to help organisations examine how security covers the entire chain and more specifically users, devices and information. We help with risk analyses, the testing and adjustment of policies, the selection of the right tools and the organisational and technical implementation of those tools.
© Peter Jurg, June 2020


